A month or so ago, I came across a security hole in an online poker network.
I’d thought about writing something about it after it had been fixed but time passed and I’d forgotten quite how major it was until I just mentioned it to someone who works for a network operator. His reaction was similar to mine when it first came to light: holy shit.
Firstly I need to say that this has definitely been fixed now and it was, rightly, treated with some urgency by the developers. However, even they didn’t know this was an issue. Nor did any of the 40+ operators on the Microgaming network (formerly Prima Poker), which includes high profile UK names like Stan James, Ladbrokes and Bet365.
All of their players were at risk.
We can only hope that because so many different technical teams had failed to spot this, fraudsters hadn’t noticed it either. After all, it’s such a fundamental security flaw, you probably wouldn’t even think to look.
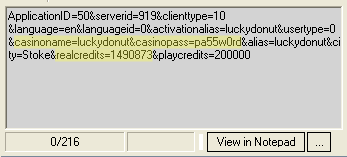
OK that’s plenty of hype. If you have the geek gene, this picture may frighten you immediately. If not, read on and I’ll explain what it means:
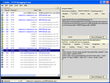
This is the text view output from an HTTP traffic debugger. It shows that player information was being sent over the network in the clear. I’ve highlighted the key parts: if you read between the ampersands, you can see my username and password (obviously this isn’t my password, I just changed it for the screen grab) and my real money balance.
Yes, at the time I did have over $14,000 in my account. I don’t any more. It was never really mine, just a fallout from testing new deposit methods. But I did sit down at a $1/$2 limit table with a five figure roll once. 🙂
From a crook’s point of view, being able to see the real money balance is a luxury that would not normally be afforded to them by using keyloggers or the less subtle approach of watching people as they key in their username and password. They would not even need to attempt to access a stolen account to know whether there is enough money in there to make it worth their while trying to run off with it.
Although I ran this traffic sniffer on my own PC, software does exist to read such traffic over a network. It’s the reason you have to look for the padlock in Internet Explorer when you’re entering credit card information. Then you know the details are encrypted before they are sent in such a way that only the web server can understand them, and not anyone listening to the network along the way.
A point I failed to get across recently when I had to pay import duty when collecting from a Parcel Force depot and they took me into the back office to enter my credit card information in an insecure web page. Seemingly, nobody had ever challenged this before.
There’s no padlock in a poker program, you just have to trust it.
The Microgaming client was in fact using SSL to send encrypted requests to the server. However along the way, they were being redirected and ended up unencrypted in the process. The redirector idea is great in theory, meaning that if an operator wants to change the location of a page or a script that’s used for their site, their players don’t need to download a whole new client for that simple change.
It’s the sheer number of requests that sent this information that was really worrying. Simply logging in to the client was secure, no username or password was visible. Accessing the banking pages was similarly secure. Whew, you may think.
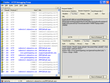
However, accessing "My Page" sent all this information in the clear. This page typically shows players their loyalty point status, allows them to change their contact information and also allows access to banking anyway. It could often be the button that players press to make a deposit or withdrawal instead of "Bank".
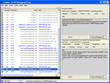
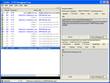
More worrying, as soon as you were logged in, a promotions page appeared in a popup. This is just a web page designed to appear in a window inside the poker program. So why would it even need to be passed information about the user? Similarly, the promotions banner that is displayed in the lobby was being passed all this information. There’s really no need.
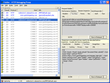
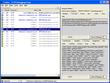
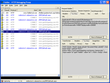
These screenshots (click to enlarge) shows all the sensitive data being passed out and then back again. At least on the way out (the bottom right pane shows an HTML form that submits these values to the actual location of the pages) it uses a secure connection.
|
My Page |
Promotions pop up |
Promotions banner |
The operator’s news page was accessed in a similar way. There’s no need at all to send a password to this page – is the latest news really only available to registered players? The responsible gaming information and support pages also received way more information than they needed. No password here, but all the other information is present. Someone must have made the decision to omit the password but to still transmit username and balance to these pages. I just can’t think what the reasoning would be for that decision.
|
News page |
Responsible Gaming page |
Support page |
So that’s six different places that a user’s account information was being transmitted. In case that’s not enough, there was one other instance that made sure anyone who was listening in for account information would not be disappointed.
In the program’s lobby – the screen where you search for which poker tables you want to play at – there is a scrolling message that is set by the operator. Because this message is intended to be updated frequently – for instance, it might say "check out our money added tournament starting at 8pm" – it refreshes every three minutes.
As this process was also transmitting all the sensitive information in the clear, all a wannabe thief would have needed to do is set up a traffic sniffing program for a few minutes and wait to be furnished with the account details. Minimum effort, maximum loot.
The screenshots I’ve posted are from Gutshot Poker. I need to stress that this operator was not at risk from this flaw – it was spotted and fixed before the player base was migrated from their previous operator. This hole would have been catastrophic to Gutshot, who operate an internet cafe where every PC is used to play online poker. A scammers paradise.
So I’ll say it again: this has now been fixed. There’s no need to kneejerk and cashout from whatever site you play at. Don’t bother the site’s support asking whether your money is safe. It finally actually is.
But if you’ve ever played on a Microgaming site in the past you really should change your password right away.

Any plain text link you can add a password or bypass the security Is Very Bad, usually called a “Get Variable”. This will also show up in the weblog and if someone was savy enough to get that, “Game Over”
The same holds true for Forms and spammers.
We fix a lot of the forms for our hosted customers, so they are not spewing out spam from our servers.
Hey Mr Pappagiorgio, no glasses tonight? 🙂
Interesting point. Even using SSL, the full query string is written to the access log on the server. It does that using Apache + mod_ssl anyway, I have no idea about other types of web server.
This only applies to GET and not POST – the data sent back from Microgaming to the operators is a POST form, but the requests to their redirector use GET. So operators have nothing to fear.
But supposing somebody on the dark side got access to the network’s systems, the thing to go for probably isn’t the user database, which would contain encrypted passwords, it would be the web logs!